OT Exposed Italy
OT (Operational Technology) consists of in a complex network of ICS (industrial control system).
The ICS describes several types of control systems and associated instrumentation used for industrial process control.
It includes systems like PLC (Programmable logic controller) , HMI (Human machine interface), DCS (Distributed control system) and SCADA (Supervisory Control and Data Acquisition).
In the ICS world we can insert all kind of device that are not like related to a process control system but use a specific and legacy protocol like devices of BMS (Building management system) and Health correlated devices (protocol like DICOM).
OT/ICS Standard secure network diagram
BMS example diagram:
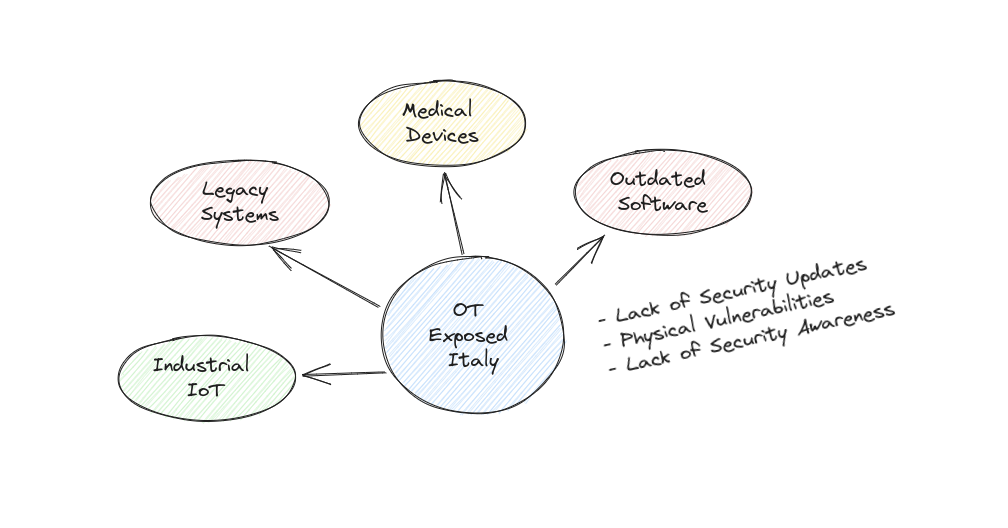
Why the ICS systems are vulnerable?
Mainly the ICS systems are vulnerable for some factor, two most important are:
Legacy Systems: Because they were designed and implemented several years ago when cybersecurity considerations were not a primary concern. These systems often lack modern security features and were not designed with robust defenses against cyber threats
Outdated software: these systems often use outdated or unsupported software components, including operating systems, network protocols, and applications.
The other factor that increases the attack surface and makes the ICS systems more vulnerable is Connectivity: With the increasing adoption of Internet of Things (IoT) and Industrial Internet of Things (IIoT) devices, ICS systems are becoming more connected to the internet and other networks.
Other factors that make ics systems vulnerable are also:
- Lack of Security Updates
- Physical Vulnerabilities
- Lack of Security Awareness
The most famous attacks in ICS systems are:
STUXNET: launched in 2016. First publically known digital weapon, development since 2005 by US government engineers to interfere with Iran atomic program; Spread through USB devices targeting Siemens industrial PLCs via control software installed on Windows systems Cause the self destruction of centrifuges used for uranium enrichment.
TRITON MALWARE: The Triton malware attack in 2017 was one of the most potentially destructive and dangerous cyber attacks on industrial control systems (ICS). This state-sponsored malware attack was discovered first in a Saudi petrochemical plant, allowing hackers to take over the plant’s safety instrument systems (SIS). This malicious code could have led to an explosion or release of toxic gas and was the first time such an attack was purposefully designed to cause loss of life. The investigation concluded spear phishing was the initial attack vector used to access the plant’s internal network, though others believe it was a misconfigured firewall.
INDUSTROYER SERIES ATTACK: Industroyer is a malware design for attack electrical power grid. First attack was performed on December 17, 2016 against Ukraine's power grid. The attack cut a fifth of Kyiv, the capital, off power for one hour. In 2022, the Russian hacker group Sandworm initiated a blackout in Ukraine using a variant of Industroyer called Industroyer2. The malware is extremely dangerous and they keep multiple backdoors for communication with threat actors.
IRANIAN STEEL INDUSTRY ATTACK: A cyberattack put Iranian steel manufacturing in the crosshairs. A hacking group by the name of Gonjeshke Darande (Farsi for Predatory Sparrow) hit the networks of three of Iran's largest steel companies: Khouzestan Steel, Hormozgan Steel, and Mobarakeh Steel. The group announced its attack on June 26th 2022 in a tweet, with video footage from inside a steel manufacturing plant showing the explosive kinetic consequences. The equipment shown is that of Khouzestan Steel, which had to shut down operations due to technical failure.
Schema of possible lacks:
Data Research & Map Generator
I’ve used mainly the OSINT portal as Shodan and Censys with about 150 queries of major ICS devices including BMS devices.
The major protocol are the follow ( not a complete list ):
- Siemens S7: Step7 Communication is a proprietary protocol that is used mainly in PLCs of the Siemens S7 family and also in the Simatic HMI panel.
- DNP3: Distributed Network Protocol is a set of communications protocols used between components in process automation systems. Its main use is in utilities such as electric and water companies.
- IEC-104: is one of the IEC 60870 sets of standards which define systems used for SCADA in electrical engineering and power system automation applications.
- Codesys: is programming interface used in multiple manufacturing devices. The CODESYS is used for automation tasks.
- EtherNet/IP: was introduced in 2001 and is an industrial Ethernet network solution available for manufacturing automation.
- Modbus: a popular protocol for ICS. It provides easy, raw access to the control system without requiring any authentication.
- Omron: Factory Interface Network Service (FINS), is a network protocol used by Omron PLCs, over different physical networks like Ethernet, Controller Link, DeviceNet and RS-232C.
- BACnet: is a communications protocol for building automation and control networks. It was designed to allow communication of building automation and control systems for applications such as heating, air-conditioning, lighting, and fire detection systems.
- Tridium Niagara Fox: the Fox protocol, developed as part of the Niagara framework from Tridium, is most commonly seen in building automation systems (offices, libraries, Universities, etc.).
The other branch of OSINT research is the medical related devices with about 120 queries. For security reasons we do not disclose the list of queries in this field because it is more critical then ICS devices.
Maps of Devices
Italy ICS devices exposed on the Internet, it can be accessed with native protocol in clear text like modbus, by means of a web interface with or without password protection.
The Distribution of organization and ISP about the previous devices:
Distribution devices by type:
Distribution devices by city (may not be precise):
Italy Medical devices correlate map, it can be accessed mainly on web interface without authentication o by means a native application protocol:
The Distribution of organization and ISP about the previous devices ( some of these are censured for security reason):
Distribution devices by city (may not be precise):
Some ICS equipment normally use the remote control application like VNC, TeamViewer, RDP etc, but are used without any security practice and left exposed on the internet. The research reveals a large number of supervising systems (as DCS, SCADA) or HMI in numerous fields from manufacturing companies, to hotels, to critical infrastructure.
Here some example with censored data for security reason:
Conclusion
The state of exposed OT devices in Italy is critical, these devices not only include plant o industries but also building management systems and Industrial IoT.
When these devices are linked to the network it must be necessary to properly configure the security and network.
For the medical devices related section we have to understand the criticality and we encourage the device owner to keep these devices protected and not free accessible from the internet.

