Medical Devices Exposed
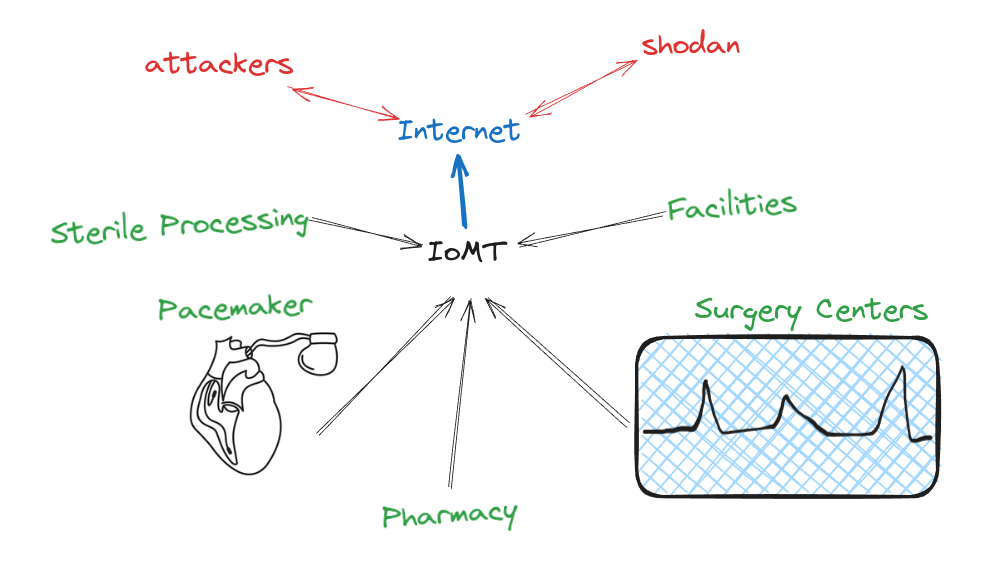
Medical devices, ranging from pacemakers to infusion pumps, have traditionally been designed with a singular purpose: to improve patient care and outcomes. Yet, as these devices become more interconnected through the Internet of Medical Things (IoMT), the cybersecurity landscape surrounding them has grown increasingly complex.
In the Healthcare landscape there are also the Medical “related things” that means all types of devices, web portals, etc that contains all patient data and can be used by the healthcare organization.
In Italy, as in many other countries, the proliferation of internet-connected medical devices has opened new avenues for cyber threats, raising concerns about patient safety, data privacy, and healthcare infrastructure integrity.
This article explains in a simple way the world of medical device cybersecurity within the Italian landscape. Through the lens of OSINT, we navigate the complex web of information surrounding medical devices, unveiling previously unrecognized risks and vulnerabilities.
Topics
- Cybersecurity Regulations and Compliance: Examine the current state of cybersecurity regulations and compliance requirements for medical devices in Italy, exploring how regulatory frameworks address emerging threats and vulnerabilities.
- Case Studies Examples: Present case studies examples of medical device and protocol vulnerabilities, emphasizing the importance of proactive security measures and timely remediation efforts.
- Medical devices exposed: Provide insights into the italian exposed landscape surrounding medical and related medical devices, discovered by OSINT methodology.
Infrastructure Medical facility
The healthcare delivery organizations analyzed in this study predominantly encompass hospitals in patient facilities equipped with onsite laboratories and specialized units like Intensive Care Units (ICUs) and burn units. These establishments host a huge amount of devices, comprising Information Technology (IT), Internet of Medical Things (IoMT), Operational Technology (OT), and Internet of Things (IoT) devices.
IT devices are primarily tasked with handling highly sensitive data, including patient health records and financial information. On the other hand, IoMT, OT, and IoT devices serve a variety of purposes, ranging from managing building automation systems and providing guest entertainment to facilitating patient monitoring and enhancing healthcare delivery processes.
Cybersecurity Regulations and Compliance:
In Italy, medical device cybersecurity is governed by various regulations and guidelines aimed at ensuring the safety and integrity of healthcare systems. One of the key regulatory bodies overseeing medical devices is the Italian Medicines Agency (AIFA), which works in conjunction with other European regulatory agencies to enforce compliance with EU directives and regulations.
European Union Medical Device Regulation (EU MDR): The European Union Medical Device Regulation (EU MDR), which came into effect in May 2021, has significant implications for medical device cybersecurity within Italy and across the EU. EU MDR aims to enhance the safety and performance of medical devices while addressing emerging cybersecurity challenges.
Key Aspects of EU MDR Relevant to Cybersecurity
- Classification of Devices:EU MDR classifies medical devices based on risk, with higher-risk devices subject to stricter regulatory requirements, including cybersecurity considerations.
- Risk Management: Manufacturers are required to conduct comprehensive risk assessments, including cybersecurity risk management, throughout the lifecycle of their devices. This involves identifying potential threats, vulnerabilities, and mitigation strategies
- Post-Market Surveillance:EU MDR mandates continuous monitoring of medical devices post-market, including cybersecurity aspects. Manufacturers must promptly report any cybersecurity incidents or vulnerabilities that could impact device safety or performance.
- Notified Bodies: Notified Bodies play a crucial role in assessing and certifying the compliance of medical devices with EU regulations, including cybersecurity requirements. They conduct audits and inspections to ensure manufacturers adhere to cybersecurity standards and best practices.
- Harmonization with Italian Regulations: Italy aligns its national regulations with EU directives, including those related to medical device cybersecurity. The AIFA collaborates with competent authorities and industry stakeholders to ensure consistency in regulatory enforcement and compliance across member states.
Challenges and Future Directions
Despite the regulatory framework provided by EU MDR, NIS2 and national regulations, challenges remain in effectively addressing cybersecurity risks in medical devices. These include the rapid pace of technological advancements, evolving threat landscape, and resource constraints faced by healthcare organizations and manufacturers.
Case Studies and Examples
Case studies provide invaluable insights into real-world cybersecurity vulnerabilities and incidents affecting medical devices. In this section, we explore case studies related to the Digital Imaging and Communications in Medicine (DICOM) protocol, insecure default passwords, and vulnerabilities in the H7 protocol, highlighting the significance of proactive security measures in mitigating risks.
Case Study 1: Vulnerabilities in DICOM Protocol
The DICOM protocol is widely used in medical imaging systems to transmit, store, and retrieve medical images and associated data. However, vulnerabilities in DICOM implementations can expose sensitive patient information to unauthorized access and manipulation.
Research and Analysis: A study conducted by multiple cybersecurity researchers analyzed DICOM implementations in medical imaging devices, uncovering multiple security vulnerabilities. These vulnerabilities included lack of encryption, improper authentication mechanisms, and susceptibility to man-in-the-middle attacks. Through extensive testing and analysis, it is possible to demonstrate the feasibility of exploiting these vulnerabilities to access and manipulate patient data.
Impact:Exploitation of DICOM vulnerabilities can have severe consequences, ranging from unauthorized access to patient medical records to tampering with diagnostic images. Such incidents not only compromise patient privacy but also undermine the integrity of medical diagnosis and treatment plans.
Mitigation Strategies:To mitigate DICOM vulnerabilities, healthcare organizations and device manufacturers should implement robust encryption mechanisms, enforce strong authentication controls, and regularly update software to address known security flaws. Furthermore, adherence to cybersecurity best practices and industry standards is essential for enhancing the security posture of DICOM-enabled devices.
Case Study 2: Insecure Default Passwords
Insecure default passwords are a prevalent security issue in many medical devices, providing unauthorized access to sensitive functionalities and data. The use of default passwords, often hardcoded into device firmware, poses significant risks to patient safety and data confidentiality.
Research and Analysis:A comprehensive study by Cylance and CISA examined the prevalence of insecure default passwords in medical devices across various healthcare settings. Researchers conducted penetration testing and vulnerability assessments on a range of medical devices, including infusion pumps, patient monitors, and diagnostic equipment. They discovered widespread use of default passwords, enabling unauthorized access to device settings and patient data.
Impact:Exploitation of insecure default passwords can lead to unauthorized device configuration changes, data exfiltration, and even disruption of critical healthcare services. Furthermore, compromised devices may serve as entry points for broader cyber attacks, putting entire healthcare networks at risk.
Mitigation Strategies:To address the risk of insecure default passwords, healthcare organizations should implement stringent password management policies, requiring users to change default passwords upon device deployment. Device manufacturers play a crucial role in ensuring that default passwords are randomized, unique, and not easily guessable. Additionally, ongoing security education and training for healthcare staff are essential to raise awareness about the importance of password hygiene and cybersecurity best practices.
Case Study 3: Vulnerabilities in H7 Protocol
Background:The H7 protocol is commonly used in medical devices for communication between healthcare systems and external peripherals. However, vulnerabilities in the H7 protocol can expose devices to remote exploitation and unauthorized control.
Research and Analysis:Multiple research and paper ( rif. BlackHat 18 ) investigated security vulnerabilities in the H7 protocol implementation of medical devices, focusing on remote code execution and command injection vulnerabilities. Researchers conducted in-depth analysis and reverse engineering of H7 protocol implementations, identifying exploitable weaknesses that could compromise device integrity and patient safety.
Impact:Exploitation of H7 protocol vulnerabilities can enable attackers to execute arbitrary commands, manipulate device settings, and extract sensitive patient information. Furthermore, compromised devices may serve as pivot points for lateral movement within healthcare networks, facilitating further exploitation of interconnected systems.
Mitigation Strategies:To mitigate vulnerabilities in the H7 protocol, healthcare organizations and device manufacturers should implement robust input validation mechanisms, sanitize user inputs, and enforce secure coding practices. Regular security assessments and firmware updates are essential to address known vulnerabilities and enhance the resilience of H7-enabled devices against cyber attacks.
Medical devices exposed
In this section we will see the exposed landscape related to medical devices in italy. It includes all the public and private hospitals listed in the “Ministero della Salute” and for all private medical clinics. Follow the distribution about the medical facilities per region:
Before the specific analisis about the exposure of medical devices and related medical devices, we can see the, in this specific case, the number of tcp port exposed ( external surface ) about the medical facilities. The count of exposed ports is very high and the good practice is to review it periodically by means of an external surface management tool to manage it.
( The medical facilities lister in the label are only the top one, the percentage is related to the sum of tcp port count that is 1750 ):
After the analysis of the total exposure we focus on the medical devices topic. For searching the devices we used the list offered by Open data contracting and from know in the OSINT field. The method used was mainly to search in the search engine like shodan, binaryedge and fofa and we build around 188 queries that are not disclosed in the current article for security reasons. Follow the example of the exposed software and device, we can see the amount of dicom and specific network device user in medical fields:
We go deep and we can see that the major part of the image viewer, study viewer and upload are without authentication with possible PHI exposure and possible data breach. Follow you can see some example:
The research also reveal a ton of web portal that used a login and this portal for best practices must be behind VPN:
Conclusion
The rapid integration of the Internet of Medical Things (IoMT) into healthcare systems has undoubtedly enhanced patient care and operational efficiency. However, this evolution has also introduced significant cybersecurity challenges that must be addressed to safeguard patient safety, data privacy, and the integrity of healthcare infrastructures. This analysis, focusing on the Italian landscape, reveals several critical insights and actionable recommendations.
Recommendations
1. Enhanced Regulatory Compliance: Strengthening regulatory compliance through continuous monitoring and updating of cybersecurity standards in line with technological advancements and emerging threats.
2. Proactive Security Measures: Implementing robust encryption, strong authentication controls, and secure coding practices across all medical devices and protocols. Regularly updating software and firmware to address known vulnerabilities and enhance the security posture of medical devices.
3. Stringent Password Management: Enforcing strict password policies, including the requirement to change default passwords upon device deployment, and ensuring passwords are randomized, unique, and secure.
4. Education and Training: Conducting ongoing cybersecurity training and education for healthcare staff to raise awareness about the importance of cybersecurity best practices and proper password hygiene.
5. External Surface Management: Utilizing external surface management tools to periodically review and manage the exposure of medical devices and related systems, reducing the attack surface and mitigating potential risks.
Future Directions
The dynamic nature of cybersecurity threats necessitates a proactive and adaptive approach. Healthcare organizations, regulatory bodies, and device manufacturers must collaborate to continuously enhance cybersecurity measures. Embracing a culture of security awareness and investing in advanced cybersecurity technologies will be vital in safeguarding the future of healthcare systems.
In conclusion, while the integration of IoMT presents numerous benefits, it also demands rigorous cybersecurity practices to protect patient data and ensure the safety and efficacy of medical devices. Through comprehensive regulatory frameworks, proactive security measures, and ongoing education, Italy can continue to advance its healthcare system while mitigating the risks associated with interconnected medical technologies.

